

What does your neighbor do for a living? Was that guy that cut you off on the high way a criminal? Who was emailing me spam? Open-source intelligence means collecting information through various public means. In other words, you can find an answer one way or another. Now the world is connected through internet advancement in technology everywhere; every person uses the social app, and data extraction can be easy now.
In this modern era, people kept memories. At each function, when they visit after Photoshoot, they upload on social media, and all information is stored on that media, which is easily accessible to people either based on cell numbers or others. In this way there all info is gathered collected within a few hours.
It can be collected through various social means like Facebook, YouTube, WhatsApp, Instagram, or any purchasing websites any marketing website. Their IP address, their search history, their area number, or maybe by their location or by code of that specific area are all included in this.
And suppose you want to gather information about the country. In that case, it may be collected by televisions radio from their books traditionally; employees profiles resume company information from website employees’ information by their portfolios, including photos and videos.

As the world is making more progress now, a way of war is changed hot wars to cold war’s now people don’t directly fight. Instead, they use tactics to fight and gather information either of a person or a specific area.
And information can also be collected by judging the need of people. It can also use positively and can also be used for business companies. Their strategies for success and information of their employees can also be seen in this perspective.so it’s up to people either use in the right way or wrong way. They have both options.
Open-source information is getting information for intelligence basis from publically to the things public used mostly.it can be used for positive mean as well and negative as well. Positively it can be used in the way that we can find the need of some people their deficiencies and can provide to them, and other is used for intelligence purpose to get trace record of someone.
It can also use to gather information to trace some people and for competition purposes also to get the record, so preparation is more.
It can also be used by armies of different countries to get the social and military records of other countries because all data are available mostly on the internet, and we can easily find the track records of persons.
Now satellites are used, and even their location can be traced due to this. Drones use this technology to locate and attack.
Books can found most of the information, articles, newspapers, and documentaries now a day’s media have much much more exposure and they try to expose everything, so this can also be used in this.

A lot of information can now be extracted by unknown sources basically purpose of this is to get information for intelligence purposes .it can be used for security purpose national security or business purposes or intelligence purposes.
Background
Data collection for intelligence purposes. Before years ago, different intelligence agencies invested millions of dollars for enemy purposes. They send spy or intelligence officers for this purpose. It was a deal of danger because any time your spy can be caught and all your information will be dusted. Your respect will be exposed, but now the world is making progress way is changed.
Revolution in the industry has changed since we are now in the digital age.
Google showing pictures that people upload has been changed by advancement in technology. Possibilities are many due to any crime gather all information regarding this collection of clues getting information wastage of time and money now mobile can be traced we can use CCTV footages all can be done within no time.
Before centuries of information detection, separate persons sent there, but now, with the help of pictures videos determined from where the location is, one can quickly identify all this.
None can be determined previous years ago, but now in the modern world, one can quickly learn what is going on in another country, so it’s a great revolution.

Open-source intelligence techniques
- Pictorial analysis
It can easily found by analysis of the picture.

Now you can do the analysis of this where this happens.
What’s around there how the land looks? What’s the model of missile and firing launcher now efficiently? Everything can be coded time location etc.
- Video analysis
Similarly, everything can be founded by seeing the video using amplifier minor minutes voices can be understood and videos can be zoomed
- Area code
Every area has a specific system by checking area code you can trace the person location from which country which city he is speaking
- Phone number research
Now the different app is there in the market which tells us whose number is this from where the person is calling now all is easy
- Linking social media account
In this modern era, every person use different social media accounts either it Instagram Facebook YouTube new Tic Tok, anything each person is connected to 3 to 4 accounts, so now information collection is quite natural because socializing is now a trend everyone is using and expose to it
- History tracer
History can be traced by visiting different people and talking with them where the person worked or where the person lived, where they play from family members all can be located.
- Online communities
Every person joined different groups where he met with different people so online communities can be a great source in finding all this, in searching for a person
- Social networking
From social networks, their account information can be gathered within no time social networking. Any incident happens quickly forwarded in this way. All news also is collected.
Example
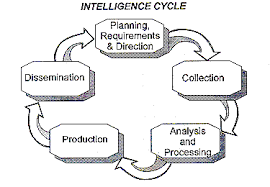
Above shows an intelligence cycle in which to achieve a targeted plan is set all requirements. The next step is collection of data, and it may be through any procedure discuss above then after collection of data analysis happened, then further processing production and dissemination of an intelligence cycle consist of these steps.
All are pre-planned, and using modern tools information is gathered.
Data collection is the central part, and it’s up to you which process you choose in data collection. Open-source information is the collection of data publicaly from public sources.
It’s up to agencies they using for positive purposes or other purposes.
Tips and tricks
Open-source information can also be used to find threats or to expose rumors. If anyone gives warning by tracing, we can easily see who the person is and what he wants, but it is the most misused and misunderstood people might take in negative.
It can find by
- Videos
- Audios
- Pictures
- Cctv cameras
- Social networking
- By id card no
- Newspaper
- Television
- Radio
- By vehicle number
- By relatives
It can be used for
- Ethical hacking
By ethical hacking like federally investigate agencies’ hack accounts to find blackmailers, it can also be used for other purposes. Ethical hacking, in this case, is appreciated because it is used for a nation to protect humans for the benefit of humanity.
Ethical hacking sometimes, agencies use to protect people from illegal hacking by hacking their devices, so it is useful. For example, if someone blackmails another person or illegally harass then by ethical hacking, we can save other people from the discomfort it’s a valuable tool if people use it positively.
- Identifying external threads
Suppose some people or thieves or terrorist organizations give a thread to people, then by a source they use like mobile phones or any other things. In that case, they can be easily traced so external threads can be easily identified. Within no time, they can be reduced it is used for the betterment of people
If threats are not discovered and minimized, it can lead to a big disaster, so to avoid this, our external threads uncoded things can be encoded.
- The negative side of open source information
People or industry can be used to damage another person like one industry trace staff and weak points of other then they can hit them on those points, and others will be damage
Another example is pictures that can be used for blackmail purposes or editing to harm others’ reputations. This is a negative side of open source information where people attack others.
- Safety
The following steps can achieve it
- use authentic apps
By using trustworthy apps, you are less exposed to hackers, and all your data is saved if you open and use unauthentic apps within no time all your efforts and image will be destroyed sometimes in educational purpose links there is hidden links by which share on your walls so try to avoid this and use the authentic app not local
- privacy policy
By using high privacy policy not allowing the app to share your details, you can remain in a safe zone before using any app read their privacy policy and change some settings so they cannot share detail with other marketing companies most of the data is given in this way before using do a quick review over it
- less giving information
Do not share information on your profile where you live from where you belong where you had work and what you are working now by keeping in secret all details you will be entirely in a safe zone.
- online shopping with an alias
try to shop online with a different name, minimizing connections back to you. Do not share your password account numbers. This way, you are more exposed to this so try to avoid, online shopping involves giving your information your address personnel data, and product quality may be varied so use authentic apps
- privacy policies on pics
Upload pics with massive privacy policy with guards so no one can use if any use quickly you get a notification on your profile
Conclusion
Every technology has its side’s effect, and advantages as well. To remain aside from disadvantages, do not upload your things personal information without reading anything and use a high privacy policy on that. Before years ago, the spy was sent to detect information that requires a lot of money, but now, with advancements in technology, everything can be easily found. People themselves upload their things, which making it easy to find the information on everything open-source information is used for intelligence purposes mostly. Still, people can use this ethically wrong, so try to make yourself secure and don’t use local apps to use high privacy policy to restrict the app not to use your information.
References
William Donovan
https://www.bellingcat.com/resources/articles/2016/07/14/a-brief-history-of-open-source-intelligence/
John Antal
http://independent.academia.edu/JohnAntal










Leave a Comment