
Editors: Knight_Writer1 and Evan Smith
I know what you’re thinking – “Interstellar Library, I am a person, not a company, why do I care?” Well, you don’t – any established company system has already set up some of Identity Management tool that allows you to have an access entity in whatever company you work at. On the off chance that you are looking to make your own business, want some insight on Identity Management tools, or just need a better solution, this article is for you.
Contents
Popular Identity Management Tools
What is an Identity management tool?
How this tool may benefit a business
What to look for in an identity management tool
The best identity management tools for your Business
What is an Identity management tool?
Identity management software manages information about software user identities and controls access to corporate resources. The overall objective of identity management software is to increase security and representative productivity. You additionally need to diminish costs while overseeing client identities and credentials.
Identity theft is a major concern for people of all ages, as innovation continues to advance. Such crimes not only result in financial losses but also misuse of personal information, which can be catastrophic for everyone.
Identity theft stances such a risk to individuals, but what amount of a danger to an association? From this point of view, organizations ought to be increasingly cautious against such criminal operations, as they can lose more by taking their personal information than common people.
There are several reasons why organizations deploy identity management software. Providing secure access to users with these tools is a daunting task but can save time and money and increase security. For this reason, the importance of ID management software continues to be in the spotlight. Identity management software has four main functions: Pure identity, user access, services, and multimedia features.
How this tool may benefit a business
Identity management tools make provisioning much easier to regulate while ensuring persistence. That is, provide and revoke access to the application according to policy. The tool also provides end-users with self-service capabilities so they can access the applications they need without delay. You can also automatically deprovision on the day you leave. In other words, on the last day of an employee’s position at a job, all their access and resources will get automatically revoked without human interaction.
These tools are liable for controlling data, remembering client information for the PC framework, data that verifies client identities, and data that depicts activities or information that can be gotten to or performed. These also manage user descriptive data and access methods. The core usefulness of IM software is given as single sign-on, multifaceted verification and access control, or as an index of ID and profile data stockpiling. These tools and IT security software are inaccessible cousins and some of the time share normal highlights. Today, this technology is experiencing an astounding change because of a pattern in identity management software that spotlights on ease of organization, incorporation and consistence.
What to look for in an identity management tool
Unlike the early days when companies had to develop their systems, identity management software was now available for purchase from many vendors. When purchasing such an answer, there are a couple of interesting points before submitting it. This includes business requirements, platform integrity, and user concerns. Aside from these, potential mix with existing frameworks should likewise be considered. However, to be an ideal tool, the basic functionality of such a solution must exist.
Distinctiveness
You have to decide whether your item bolsters numerous directory types, for example, LDAP, UNIX/Linux, and Microsoft Active Directory. You will need authentication methods such as SecureID, X509 certificates, biometrics, and the ability to support existing applications, servers, and databases.
Operational management
Users must be able to update their profile data after logging in to the system. Similarly, individual passwords should be able to be reset with minimal administrator intervention. There must likewise be a mix of existing client records so chairmen can deal with the framework from anyplace utilizing the web interface.
Accessibility/Scalability
Like other software arrangements, identity management software must be adaptable and ready to deal with huge quantities of clients while looking after execution. The volume of framework clients can increase from exercises, for example, mergers and acquisitions. You need to support multiple servers, along with load balancing and clustering for failover. Such an identity management system must have a database that can securely store audits, report logs, and flat files. The reflecting capacity is likewise a helpful capacity to secure client information.
Access management
The integration of the system’s access component must be that of the identity component. This allows access policies to be updated automatically if the user ID changes. You need to be able to create multi-step access policies without coding. Role conflicts must also be detected without granting such easy-to-execute privileges.
Reliable
A perfect identity management arrangement ought to have the option to include, modify, or erase clients from a solitary dashboard. You additionally need the capacity to keep in touch with numerous client identity stores based on strategies and jobs. Aside from these, such software must help government identity norms, for example, Liberty Alliance, WS-Federation, and SAML 1.1. Make an incorporated workflow for manual endorsement.
The correct identity management tools for your business
Today, the period of cutting-edge identity management is a significant focal point of associations, utilizing just best in class tools to shield client identities from ruptures. Be that as it may, the equivalent is valid for the individuals who take part in illegal activities, for example, hacking and identity theft. That’s why software developers are devising more robust systems to improve their games and protect their business. Below is a list of the best identity management tools.
MiniOrange Identity Management

MiniOrange, a cloud-based identity management arrangement, furnishes endeavors with strong features remembering single sign-for, multifaceted verification, social login, LDAP, and directory mix with AD. The framework is well known for believed organizations around the globe for its IAM administrations gave to Salesforce, Google Apps, Office 365, Amazon AWS, Dropbox, Joomla, and the sky is the limit from there. Other key features incorporate access demand management, password and job management, client activity observing, and client provisioning.
MiniOrange is available in a variety of pricing modules at lower prices. Free trials are also available for those who want to try first.
ForgeRock for Identity Management
The ForgeRock Identity, an information management tool, is famous for its capacity to coordinate with existing business frameworks. A highly customizable sports module that offers additional features. Growing companies can benefit greatly from this software because the software is scalable and can grow like a company. This is because you can add nodes during the run with minimal impact on the environment. Similarly, you have the flexibility to support almost any certified product and federation protocol. Vendors provide excellent support and respond quickly to those who need a patch or bug fix.
Price information of ForgeRock Identity Platform is not disclosed. You must contact the vendor directly to request a quote.
WSO2 Identity Server
WSO2 Identity Server is an identity management tool that can store many identities in business systems. Designed for use by businesses of various types and sizes. Various tools cover APIs, enterprise web apps and services. The solution can be deployed on-premises or via the cloud and supports both Windows and Mac platforms. Aside from the fact that vendors provide training for novice users, they are known for their ease of use because they come with a simple dashboard that provides access to all features. With the software, the single sign-on feature eliminates the need for users to remember a different password for each login. Vendors provide robust support that is available all the time.
WSO2 Identity Server is available in a variety of pricing plans at lower costs. A free trial version is also available for those who want to explore the features of the software first.
Centrify Identity Service
The identity management solution Centrify Identity Service is a popular tool with many features such as custom reports, scripts and workflow provisioning. Entry-level pricing also supports multi-factor authentication. Setup is easy. All you need to do is create an account, create an account, and link to your corporate email. Connect with other providers such as Microsoft Azure AD and Okta. This is very useful for companies that need to certify contract staff and partners. The software Cloud Connector provides sync functionality anytime, anywhere. The system automatically generates a default domain and allows users to add their domain for authentication. You can also automatically provision users and extend them to roles in third-party apps.
The Centrify Identity Service can be purchased a little bit more in price than previous ones. Add-ons are available for those who want to enjoy more features.
ADManager Plus
ADManager Plus is known for its ease of use. This simplifies the Active Directory administration tasks that administrators and help desk technicians face every day. The software can be easily implemented on machines running on Windows and is suitable for companies of various types and sizes. Other features include the organization of professional and personal contacts, monitoring employee activity and productivity, and managing large numbers of user accounts. And you have full control over your workflow and operations.
AdManager Plus is available on a price quote basis. Contact your vendor for pricing information.
Auth0 for information management
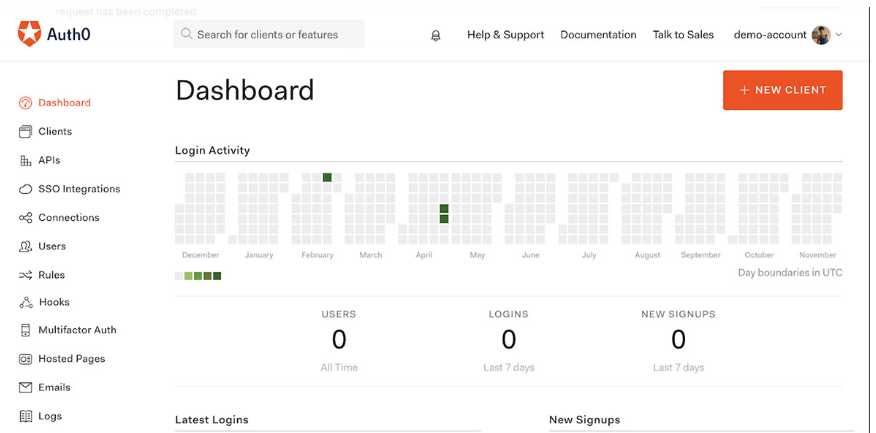
The identity management stage Auth0 is a cloud-based framework that handles venture client and identity management forms. You can oversee tasks, for example, enlistment, login, password reset, to give some examples. Sellers esteem security utilizing just best in class security technology to guarantee that all client information and passwords are put away safely. The arrangement is basic and significantly easier to utilize, enabling clients to sign in utilizing Facebook and Github, among numerous different stages. The refined dashboard enables clients to see late logins, recruits, and all outnumber of clients. Thus, customer arrangement, webhooks, logging, and client investigation are conceivable.
Auth0 is accessible in an assortment of estimating choices beginning at $ 13 for each client for every month. For big business clients, you should contact the seller legitimately at a cost statement. A free version with all the basic features of the tool is also available.
LogMeIn Pro for IM

LogMeIn Pro is an identity management software with a greater number of functions than an ordinary password and client management tools. It offers full remote access to your PC from any program, Click2Share tool, record move interface, and the capacity to print reports from a remote machine. Users simply select a file and anyone can email the access link to give colleagues access to any file in the host system.
Azure Active Directory
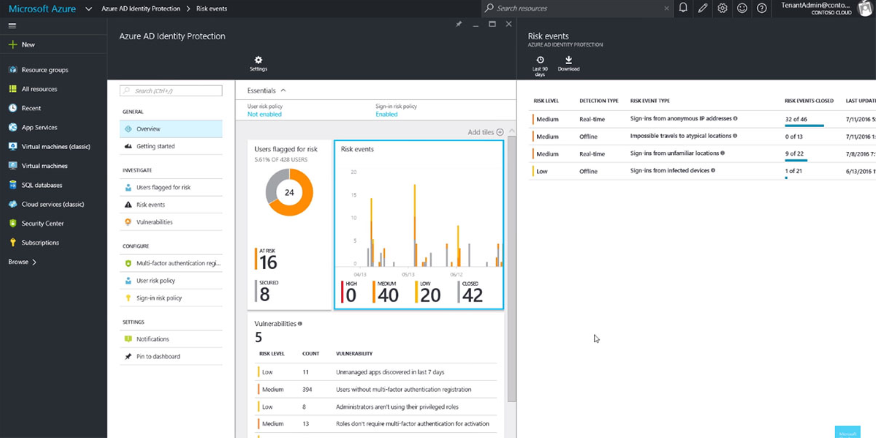
Azure Active Directory is a powerful identity management stage that coordinates with both Active Directory and Office 365 and is at present considered the best financially savvy multifaceted verification tool. The good thing about the system is that it provides it to the user. Gain valuable insights with advanced reporting capabilities to further improve your identity management process. This is a feature not found in most software in this category. Also, a service application used by users to manage user IDs and used by Software-as-a-organizations.
Integrating office 365 into any environment has become a seamless process. The benefits of Microsoft Azure Active Directory pricing plans are not available on vendor sites. You have to go to the official website and ask for a value quote.
Microsoft Forefront
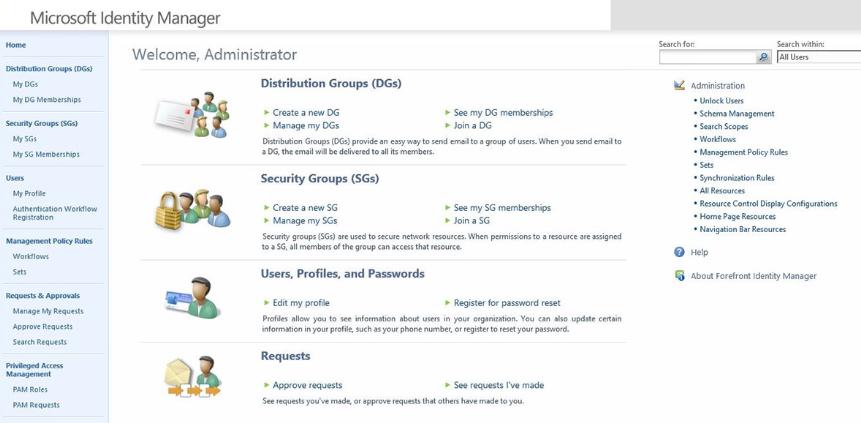
Forefront is Microsoft’s identity management arrangement known for easy reconciliation with SharePoint. This reconciliation enables framework heads to productively oversee client identities and make identity workflows from one interface. Similarly, security management and distribution of group profiles can assist users. The stage has various self-administration tasks, including password and profile management. All procedure management activities are performed from an easy-to-utilize web-based interface that can be utilized by anybody with involvement in Microsoft tools.
Microsoft’s Forefront Identity Manager is sold on a for every client basis. You can request pricing information by visiting the vendor’s official website.
Oracle Identity Manager
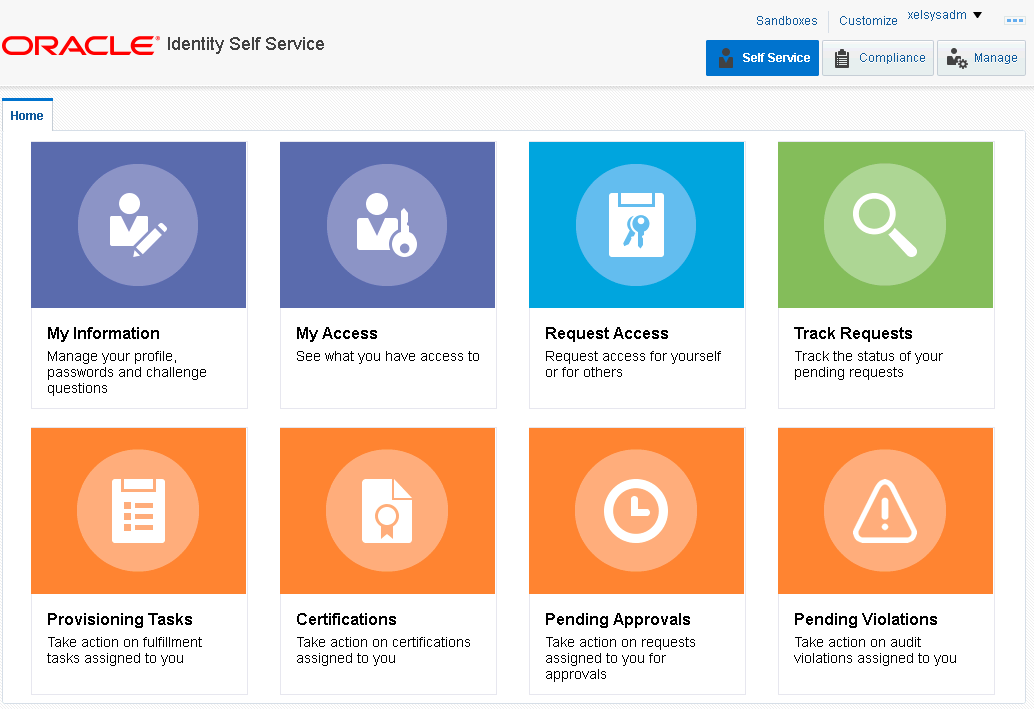
Oracle Identity Manager is Oracle’s own Identity Management Interface. It allows for custom plugins, automatic AD and LDAP provisioning, as well as integration into most Human Resource Interfaces. Oracle Identity manager is a large scale platform while can support businesses medium and large. Its ability to connect all your company’s services makes it an essential component to every user’s company lifecycle. Pricing for this product is meant for large entities – https://www.oracle.com/assets/technology-price-list-070617.pdf
More information on this OIM can be found here: https://www.oracle.com/middleware/technologies/identity-management/
Conclusion:
Identity Management software is an essential component of your systems if you have to manage users across multiple platforms. If you require single sign-on solutions, a lot of the above can make it so you only need to log in once to access all of your resources – saving you and your company time and money.
Do you have any experience with any of the above products? We would like to encourage you to share your experience and opinions!
The contents of the screenshots are taken courtesy of their respective software owners. No financial representation was made by any of these products. Cover Image by Photo Mix from Pixabay










Awesome post! Keep up the great work! 🙂
I truly appreciate this post. I have been looking all over for this! Thank goodness I found it on Bing. You have made my day! Thx again
I really loved what you had to say, and more than that, how you presented it.
Thanks again for the blog post. Really looking forward to read more. Keep writing.
Very neat post.Much thanks again. Great.
Major thanks for the blog post. Great.